1. Introduction
National Institute of Standards and Technology (NIST) Cyber Security Framework provides for comprehending, managing, and expressing cybersecurity risk to internal and external stakeholders. This framework provides us a wide variety of ways to feed the unique cybersecurity needs of organizations. The framework provides a common mechanism for organizations to describe current cybersecurity posture, describe the target state for cybersecurity, assess progress towards the target state. Communicate among internal and external stakeholders about cybersecurity risk.

2. Framework Overview
The risk-based approach put forward by the framework to handle cybersecurity risks is composed of three parts:
- Framework Core
The Core contains industry standards, guidelines, and practices that allow for communication of cybersecurity activities between executive level and implementation/operations level. The Framework Core consists of five continuous functions- Identify, Protect, Detect, Respond, Recover. - Framework Implementation Tiers
Tiers define the degree to which an organization’s cybersecurity risk management practices exhibit the characteristics defined in the framework. They characterize an organization’s practices over a range, from Partial (Tier 1) to Adaptive (Tier 4). - Framework Profile
The Profile aligns the standards, guidelines, and practices to the Core in an implementation scenario. Profiles can be characterized as Current Profile (“as is “ state ), a Target profile (“to be” state). These profiles are further used for the measurement of progress.
3. Framework Components
In this section, we will explain in detail the 3 components of the NIST framework:
- Framework Core
The Core is not a checklist of actions to perform; rather, it mentions key cybersecurity outcomes identified as helpful in managing cybersecurity risk. The Core comprises of three functions as mentioned below:- Functions
Functions express management of cybersecurity risks, enabling risk management decisions, addressing threats, etc. of an organization. These functions are:- Identify
Identify the organization’s capabilities to manage
Cybersecurity risk to systems, people, assets, data.Examples of outcome categories are Asset Management, Governance, Risk Assessment, etc. - Protect
Protect and ensure the delivery of critical services by developing and implementing the required safeguards.
Examples of outcome categories include Awareness and training, Data Security, Identity Management, and Access Control. - Detect
Detect the occurrence of a cybersecurity event by implementing appropriate measures. Examples of outcome categories are Anomalies and Events, Security Continuous Monitoring, and Detection Processes. - Respond
Respond to a detected cybersecurity incident and develop and implement appropriate activities. Examples of outcome categories are Communications, Analysis, Mitigation, and Improvements. - Recover
Recover and restore any services that were affected by any cybersecurity incident. Examples of outcome categories are Recovery Planning, Improvements, and Communications.
- Identify
- Categories
Functions are further grouped into cybersecurity outcomes closely tied to programmatic needs and particular activities.Examples of categories are Asset Management, Identity Management, and Access Control, etc. - Subcategories
Categories are further divided into outcomes of technical and/or management activities. Examples include: Data at-rest is protected. External information systems are cataloged. - Informative References
There are sections of standards, guidelines, and practices common among sectors that define a method to achieve outcomes associated with each subcategory.
- Functions
- Framework Implementation Tiers
The Tiers identify the level up to which cybersecurity risk management is informed by business needs and is integrated into an organization’s risk management activities. Tier definitions are as follows:- Tier 1: Partial
- Risk Management Process
Risk Management processes are not approved and executed as a policy. Cybersecurity activities are notprioritized by business requirements and are not informed by organizational risk objectives, threat environment, etc. - Integrated Risk Management Program
Limited Awareness of cybersecurity risks at organizational level with an implementation of risk management on a case by case basis. - External Participation
The organization does not share or receive information from other entities and is unaware of cyber risks possessed by its products and services.
- Risk Management Process
- Tier 2: Risk-Informed
- Risk Management
Risk management practices are approved but are not formulated as an organization-wide policy. Prioritisation of activities is directly dependent on organizational risk objectives, the threat environment, or business/mission requirements.
Integrated Risk Management Program
There is Awareness of cybersecurity risks at the organizational level, but an organization-wide approach to risk management is missing. Cybersecurity information is shared informally.- External Participation
The organization receives information from external entities and generates some of its own information, but does not share information with others.
- Risk Management
- Tier 3: Repeatable
- Risk Management Process
Risk Management processes are approved as policy. They are regularly updated based on changing business requirements. - Integrated Risk Management Program
An organization-wide approach to manage cybersecurity risks in implemented with defined risk-informed policies, procedures, and processes. - External Participation
Organization shares and receives information from other entities regularly. It is aware of the risks associated with products and services it provides and uses.
- Risk Management Process
- Tier 4: Adaptive
- Risk Management
Cybersecurity practices are based on lessons learned from current and previous cybersecurity activities. Thus, the organization adapts to changing threats and technology updates and responds in an effective manner. - Integrated Risk Management Program
Cybersecurity risks are monitored in a similar way as any other risk in an organization. Cybersecurity risks are managed using organization widely implemented risk-informed policies, processes, and procedures. - External Participation
The organization receives, generates, and reviews prioritized information to provide information about risks as threats and technology make progress. The organization shares information internally as well as externally with other collaborators.
- Risk Management
- Framework Profile
The Framework Profile is an arrangement of Functions, Categories, and Subcategories on the basis of business demands, risk tolerance, and resources of the organization. It helps organizations to reduce cybersecurity risks that affect the organization’s goals. Many organizations may choose multiple profiles based on their needs.
The current Profile indicates outcomes that are being achieved, and the Target profile indicates outcomes needed to be achieved. These profiles can be compared to indicate gaps to be addressed to meet cybersecurity objectives.
- Tier 1: Partial
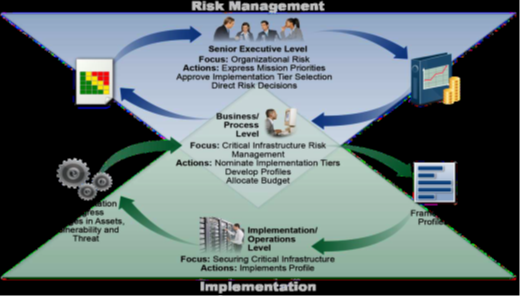
4. Coordination of Framework Implementation
- Commonly the flow of information is between the following levels in an organization
- Executive
- Business/Process
- Implementation/Operations
Writer: Kunal Babbar in the mentorship of Karan Srivastava