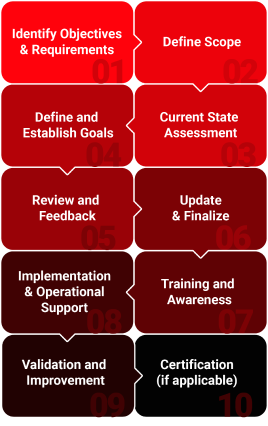
ISO 27001 is a certification standard that establishes a framework for organizations to implement a robust Information Security Management System (ISMS). It requires organizations to identify and assess risks to their information security, develop and implement appropriate controls, and continuously monitor and improve their security practices. ISO 27001 certification demonstrates an organization's commitment to protecting sensitive data and meeting industry best practices for information security.
ISO 27001 is an internationally recognized standard for information security management systems (ISMS). It provides a framework for organizations to protect their sensitive information and ensure compliance with relevant laws and regulations. Here are the key components of ISO 27001 compliance
A formal document outlining the organization's commitment to information security and its objectives.
Identifying and assessing potential threats and vulnerabilities to the organization's information assets.
Implementing a range of technical, organizational, and administrative controls to mitigate identified risks.
Establishing a systematic approach to managing information security, including processes, procedures, and documentation.
Regularly monitoring the effectiveness of security controls and conducting periodic reviews to identify areas for improvement.
Implementing procedures for handling and responding to security incidents.
Ensuring compliance with relevant data protection laws and regulations, such as GDPR and CCPA.
Assessing and managing risks associated with third-party service providers.
Providing security awareness training to employees to foster a security-conscious culture.
Conducting regular audits to assess compliance with ISO 27001 and seeking certification from an accredited certification body.
ISO/IEC 27001 is a strategic advantage in today’s data-driven world. Implementing it helps streamline security practices and align with global standards. Achieving certification shows your organization upholds a world-class ISMS, adhering to international best practices.
ISO 27001 provides a structured approach to managing information security risks, helping organizations protect sensitive data and prevent breaches.
By demonstrating a commitment to data protection, ISO 27001 compliance can enhance customer trust and loyalty.
ISO 27001 can help organizations comply with various data protection regulations, such as GDPR and CCPA, reducing the risk of fines and penalties.
Organizations that are ISO 27001 certified may have a competitive advantage in the marketplace, as customers and partners often prefer to work with companies that have demonstrated a strong commitment to data security.
By identifying and addressing potential risks, ISO 27001 compliance can help organizations reduce the likelihood of financial losses and operational disruptions.
ISO 27001 can help organizations streamline their security processes and improve operational efficiency.

We believe that no two organizations are alike. We begin by thoroughly understanding your specific needs to develop tailored solutions that address your unique challenges. Our approach is innovative and personalized, unlike copy-pasting one-size-fits-all templates.
We establish a flexible framework that supports expansion of a wide range of compliance requirements, such as PCI-DSS, SOC2, SOX, GDPR, HIPAA, and others, to meet your organization's current and future needs.
We offer integrated solutions to reduce the effort and cost of operating multiple compliance frameworks. We integrate management systems from various domains, such as information security, data privacy, business continuity, quality, maturity models, etc.
We collaborate with your team and empower them through comprehensive training and knowledge transfer and enable them to effectively implement, operate, and maintain the solutions we deliver.
We offer ongoing support and are committed to addressing any questions or concerns your team may have while implementing or operating our solutions for an extended period after delivery.
With over two decades of industry experience in different domains, industries, and geographies, we provide practical and sustainable solutions that align with your business objectives.

Our team boasts a wealth of experience and holds numerous industry-recognized certifications, including CISSP, CIPM, CIPP, CISM, CCSP, CGRC, CDPSE, CISA, CRISC, OSCP, CEH, and many more.

Our commitment to your success extends beyond the project delivery. We provide full operational support for an added peace of mind that enables you to concentrate on your strengths while we handle the complexities.


We use cookies to ensure you get the best experience on our website.