Scoring Vulnerabilities: CVSS

Introduction
Vulnerabilities are weaknesses that can be exploited to compromise the security of assets. They are weaknesses in an information system, internal controls, or implementation that could be exploited.[1] There can be many vulnerabilities in a system/organization, which need to be identified, defined, and prioritized in order to provide the necessary knowledge, awareness, and risk background. One way to prioritize these vulnerabilities is by scoring these vulnerabilities. Prioritizing vulnerabilities helps us to identify the order in which these vulnerabilities need to be accessed and remediated.
Common Vulnerability Scoring System
[2]The Common Vulnerability Scoring System (CVSS) gives an approach to catch the foremost attributes of a defenselessness and produce a numerical score mirroring its seriousness. The numerical score would then be able to be converted into a subjective portrayal, to help associations appropriately survey and organize their defenselessness the board forms.
It is managed by FIRST.org. The current version of CVSS is 3.1.
The (CVSS) catches the essential specialized attributes of programming, equipment, and firmware vulnerabilities. Its yields incorporate numerical scores demonstrating the seriousness of a weakness comparative with different vulnerabilities.
3. Metrics
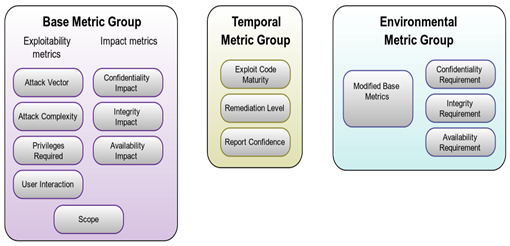
- Base Metric Group
This group represents the characteristics that are constant over time and across user environments. - Exploitability Metrics
They depict the ease of technical means by which vulnerability can be exploited.- Attack Vector
(Network>Adjacent>Local>Physical)
This depicts the means by which an attacker can exploit the vulnerability. The more the score, the more remote the attacker can be. - Attack Complexity
(High>Low)
This describes the conditions not under the control of attackers which need to be present for the vulnerability to be exploited.
- Privileges Required(High>Low>None)It informs about the level of privileges required for the attack.
- User Interaction(Required, None)It captures whether any human interaction, instead of the attacker, is required for the attack.
- Scope(Unchanged, None)It defines whether a vulnerable component, when exploited, affects other components or company or not.
- Attack Vector
- Impact Metrics
They depict the consequences of a successfully exploited vulnerability on the component on which attack is performed. - Confidentiality Impact
(High>Low>None)
It represents the impact on the confidentiality of the information resources managed by the component exploited by the attack. - Integrity Impact
(High>Low>None)
It represents the impact on the availability of the information resources managed by the component exploited by the attack. - Availability Impact
(High>Low>None)It represents the impact on the confidentiality of the information resources managed by the component exploited by the attack.
- Temporal Metric Group
- Exploit Code Maturity(Not Defined, High, Functional, Proof of concept, Unproven)
It measures the likelihood of a vulnerability being exploited. It is based on the current state of exploit techniques, exploit code availability, to exploit a given vulnerability. - Remediation Level
(Not Defined, Unavailable, Workaround, Temporary Fix, Official Fix)
The typical vulnerability is unpatched when initially published. Workarounds or hotfixes may offer interim remediation until an official patch or upgrade is issued. Each of these respective stages adjusts the Temporal Score downwards, reflecting the decreasing urgency as remediation becomes final. - Report Confidence(Not Defined, Confirmed, Reasonable, Unknown)It measures the degree of confidence in the existence of vulnerability and credibility of the known technical details.
- Exploit Code Maturity(Not Defined, High, Functional, Proof of concept, Unproven)
- Environmental Metric GroupThese metrics have a unique value for different user environments.
- Security Requirements(CR,IR,AR)(Not Defined, High, Medium, Low)
These metrics affect the score depending on the importance of the affected IT asset to a user’s organization, measured in terms of Confidentiality, Integrity, and Availability. - Modified Base Metrics
These metrics override the individual Base metrics on the basis of a user’s environment.
- Security Requirements(CR,IR,AR)(Not Defined, High, Medium, Low)
4. Scoring
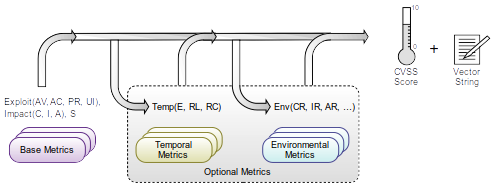

5. Closure
[3]The advantages of CVSS incorporate the arrangement of a normalized seller and stage skeptic weakness scoring philosophy. It is an open structure, giving straightforwardness to the individual attributes and philosophy used to determine a score. The CVSS permits associations to organize which vulnerabilities to fix first and measure the effectiveness of the vulnerabilities on their frameworks.
Writer: Kunal Babbar in the mentorship of Karan Srivastava
Recommended Posts
-

Mysteries of the Dark Web
Jun 1, 2021 -

Has COVID paved the way for Work From Home culture?
Sep 21, 2020 -

Ripple20 Vulnerabilities
Sep 21, 2020 -

TOOLS FOR WEB APPLICATION SECURITY PART-2
Aug 1, 2020